BBG Tech:That One Time I Hacked My Mom’s iPhone Camera, Ethically, Of Course
by Aiden Satterfield
My mom, Crystal Good, the owner of BBG, got hacked one time. You’re probably thinking the owner of BBG got hacked and her kids are cybersecurity nerds? Well, it was an agreed-upon cybersecurity test, kind of. I said Hey Mom, check this link out. Something related to Appalachia. And, BOOM (I knew that would get her), and of course, she clicked it, the link then said, “Can we allow access to your camera?” She allowed access without thinking, and below is a step-by-step walkthrough of what happened.
Some time ago, I conducted a personal cybersecurity experiment that ended with my mom’s iPhone camera streaming directly to my Kali Linux machine. It sounds intense, but it was entirely ethical, she permitted me, kinda.. though she didn’t fully understand what “just clicking allow” could do. Let’s walk through how something like this could happen.
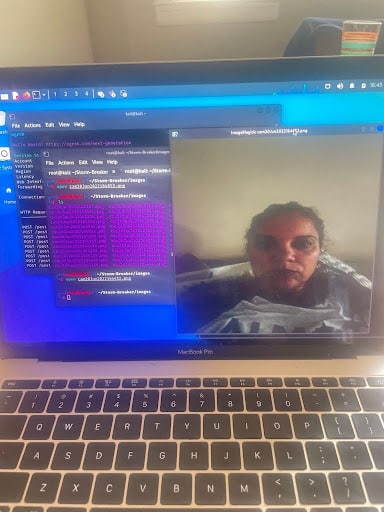
To execute the test, I used a tool called Storm-Breaker, available on GitHub at ultrasecurity/Storm-Breaker. I cloned the repository using:
git clone https://github.com/ultrasecurity/Storm-Breaker.git
cd Storm-Breaker
Ls (to confirm install.sh and st.py are there)
sudo ./install.sh
From there, Stormbreaker is now installed. I launched the tool using python3 st.py, which set up a local control panel. The tool integrates with Ngrok, so you will need an Ngrok account —a tunneling service that exposes localhost ports to the internet, effectively bypassing NAT and firewall restrictions. This allowed me to generate a public-facing URL to send to her device.
When my mom opened that link I created through Ngrok and clicked “allow” on the camera and location permissions, the tool captured snapshots from her webcam and sent them back to my system.
Here’s the truth: most attackers aren’t writing custom code or inventing new exploits. They’re using prebuilt, open-source tools just like Storm-Breaker. Many of these tools come with plug-and-play functionality: Type a few commands, send a link that they know will intrigue you, wait for someone to give permission, and that’s it.
And it works way more often than people think, especially with tools that use social engineering. Attackers don’t need to be geniuses. They just need you to be distracted, curious, or overly trusting.
Aiden Satterfield is a cybersecurity graduate and athlete from Walsh University, and a native West Virginian.
For more information or to engage with BBG Tech contact: info@blackbygod.org. Let’s continue to inspire, inform, and foster an environment where diversity and innovation thrive in the tech industry.
If you appreciate BBG's work, please support us with a contribution of whatever you can afford.
Support our stories




