The Reality of Zero Trust Security: Why “Trust No One” Is Harder Than You Think

By Aiden Satterfield | BBG Tech
Zero Trust architecture (ZTA) has been the security term thrown around for years, but it’s finally hitting mainstream adoption. Enterprises and startups alike are adopting the mantra never trust, always verify, but the reality is messier than the powerpoint marketing slides suggest.
Zero Trust flips the old network-security model on its head. Instead of assuming anyone inside the corporate network is safe, every access request—whether from an employee, a contractor, or even a server, must be verified. This includes multi-factor authentication, device health checks, least-privilege access, and continuous monitoring. Sounds solid, right? But implementing it is far from trivial.
Here is a good diagram that Microsoft posted not too long ago that explains it well. Everything needs to be verified before getting access.
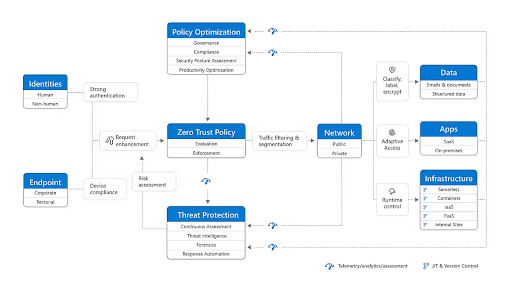
Here’s the catch. Legacy systems, sprawling networks, and complex workflows make enterprise Zero Trust adoption painful. Mapping every user, device, and resource is a huge undertaking, and older applications often can’t handle modern authentication protocols. Startups face a different challenge, convenience vs. security. A mentor of mine told me those two don’t work well with each other. Sadly something will be sacrificed. Small teams want frictionless access to cloud services, and aggressive Zero Trust controls can push employees toward shadow IT or workarounds that defeat the whole purpose.
The threat landscape is real. Without careful implementation, Zero Trust can create blind spots. Policies might block legitimate requests or, worse, fail to block attackers who find loopholes in workflows or misconfigured privileges. Continuous monitoring generates a flood of alerts that security teams must sift through, too many false positives and critical signals can get lost.
You can deploy MFA, segmentation, and endpoint monitoring, but without clear policies and user training, the model collapses. And just like any security measure, it’s not static. Attackers adapt, and ZTA requires ongoing tuning, auditing, and evaluation to remain effective.
So what does this mean for your organization? Zero Trust is definitely powerful, but it’s not a magic button. Treat it as a framework, not a product. My suggestion would be start small, verify continuously, and balance security with usability. For enterprises, that means segmenting sensitive systems, integrating identity providers, and monitoring endpoints.
The bottom line: trust must be earned constantly, inside and outside your network. Zero Trust is here. And it’s not going anywhere. It increases the level of security significantly and people are tired of getting compromised, I understand.
But it’s only as effective as the people, processes, and policies that implement it. Done right, it significantly reduces risk. Done wrong, it’s a bureaucratic headache, and a false sense of security.
In practice, this means Zero Trust is more about discipline than tools. It’s about continuously questioning who-or what-should have access, and never assuming safety just because someone or something is “inside.” If you’re planning to adopt ZTA, buckle up: it’s a journey, not a checkbox.
If you appreciate BBG's work, please support us with a contribution of whatever you can afford.
Support our stories




